With the race to digital transformation, the transition to mobile working and the necessity of working from home, digital assets are spread beyond the enterprise, leaving sensitive data and applications exposed to criminal activity. Yet unless you know where you stand and where the vulnerabilities lie, you can’t properly protect your most valuable assets.
The Threat Management Maturity and readiness quotient provided by Tata Communications enables your enterprise to understand how vulnerable you are to cyberthreat and pinpoint any areas for improvement. Based on your answers, you’ll receive personalised recommendations to help you take the next steps towards your 360° security readiness, enabling you to plan a course of action to stay safe – before the threat becomes a reality.
To help organisations better prepare for their Threat Management journey, Tata Communications has prepared a structured framework of questions that enables you to assess your organisation’s readiness to cyberthreat. We examine your primary objectives for looking at cyberthreat management, including how your organisation currently handles cybersecurity incident management, focusing on three key areas:
Start the assessment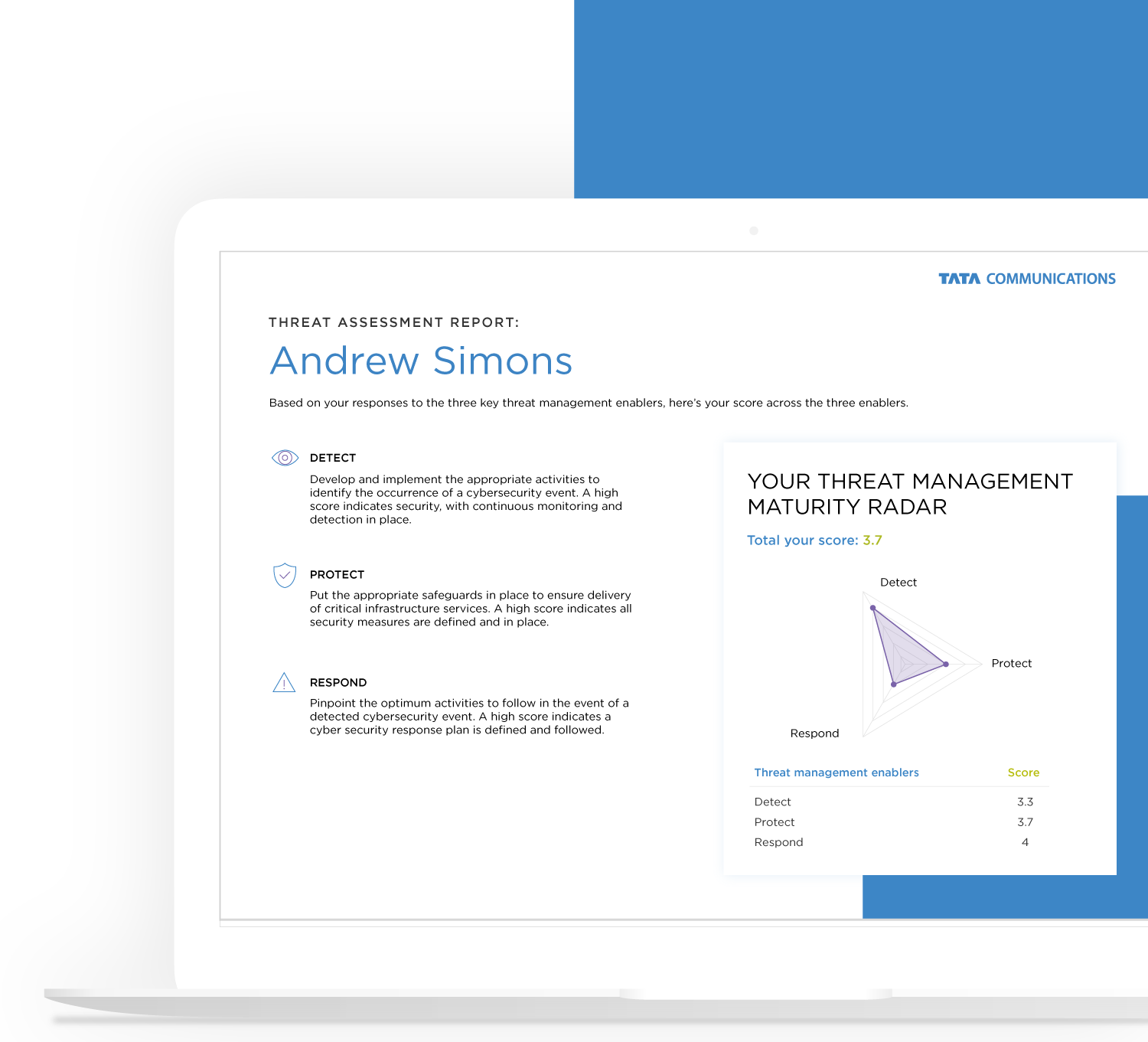
We will assess how often your IT performs threat hunting exercises and your primary sources of information for threat hunting. The survey will take into account any commercial threat intelligence feeds that you currently use, and whether false positives pose a significant problem for you.
In this stage of the survey we look at the specific security controls that you have deployed, along with any skills gaps you can identify. Red Team and threat modelling exercises will also be taken into account.
Finally, we look at how you deal with the threats. From online dashboards to ITSM platforms and incident response automation, we look at your ongoing projects to identify any areas still to be addressed.
Following the survey, you will be given a score based on industry best practices. The scoring classifies organisations into five maturity levels:

By focusing on the three key areas – Detect, Protect and Respond – you can act on the findings from the survey report to guard against threats and protect your data, your organisation and your reputation from cyberattack.
Your report will contain a number of specific recommendations designed to help your enterprise get proactive, get control and get ahead.
